JSON Web Token Authorization Mechanism¶
Our platform uses OAuth2 protocol with JSON Web Tokens (JWT) for authentication. This mechanism supports Password, RefreshToken, and ClientCredentials flows. Tokens issued by the platform are signed with a private key and can be validated using either a public certificate or an Authority URL. Configuration for certificates and Authority URL is specified in the Auth section of the appsettings.json file.
The guide includes the following steps:
- Creation of self-signed certificates for signature and validation of tokens using OpenSSL.
- OAuth2 authorization using client credential flow.
Create Self-signed Certificates for Signature and Validate Tokens Using OpenSSL¶
To create self-signed certificates for signature and validate tokens:
-
Generate a private key:
-
Run:
-
Specify a password for the private key in the certpass.txt file.
-
-
Generate a certificate by running:
openssl.exe req -x509 -nodes -days 3650 -key virtocommerce.key -config certconfig.txt -extensions req_ext -passin file:certpass.txt -out virtocommerce.crtExample of certconfig.txt file
[ req ] default_md = sha256 prompt = no req_extensions = req_ext distinguished_name = req_distinguished_name [ req_distinguished_name ] commonName = virtocommerce.com countryName = RU stateOrProvinceName = Kaliningrad organizationName = Virtocommerce [ req_ext ] subjectKeyIdentifier = hash authorityKeyIdentifier = keyid:always,issuer keyUsage=critical,digitalSignature,keyEncipherment extendedKeyUsage=critical,serverAuth,clientAuth subjectAltName = @alt_names [ alt_names ] DNS.0 = virtocommerce.com -
Create PFX container for private key and certificate by running:
Note
The system does not accept private keys smaller than 2048 Bits.
OAuth2 Authorization using Client credential flow¶
To authorize client applications (for example, Storefront), use the Client credential flow mechanism of OAuth2 protocol:
- In the main menu, click Security.
- In the next blade, select OAuth applications.
- In the next blade, click Add in the toolbar.
-
In the next blade, fill in the following fields:
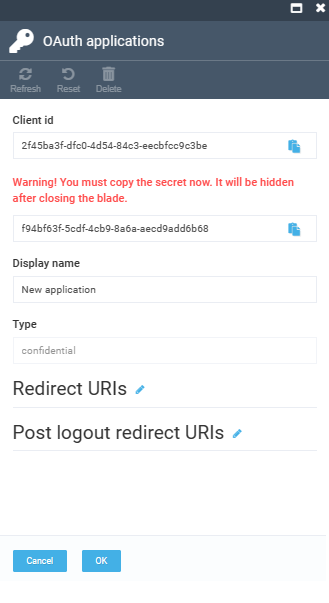
Note
Client Id and Client secret are generated automatically. Save them, as the system will not allow you to view already saved Client secret.
Note
You can change Client Id and Client secret only during the creation of a new application (you will not be able to change them later). You can also specify a Display Name for more information.
-
Click OK to save the changes.
New OAuth2 client has been created. Now the client application is able to authorize requests to the API using the previously created Client Id and Client secret.
In Storefront, all you need to do is specify the Client Id, Client secret created earlier, and the authorization server in the Endpoint section of the appsettings.json file.